"Security" companies and abuse e-mails
February 7, 2017
The Internet, like almost anything invented by humans, has been used to conduct malicious acts. This can be something not really important like comment spam, all the way to very important cases that are usually investigated by law enforcement like private information and user data theft. While running a Tor Exit Node, I had the chance to witness a lot of that stuff. This, unfortunately, isn’t an easy problem to solve, and most approaches have failed.
In order to handle abusive behavior in an easier and better way, most, if not all, IP Addresses, be it v4 or v6, come with a so-called “abuse mailbox”. This is a special e-mail address, typically in the form of abuse@example.com, which is included in the IP whois records. Finding this IP Address, especially for organizations in Europe and the Middle East, is extremely easy, but it can also prove difficult in organizations in, say, Latin America, where the whois records are at best terrible.
This e-mail address is usually for small, not so important cases, which are usually solved by a network administrator, and not necessarily law enforcement agencies. It is a first point of contact to let the network operator know that some of their customers are misbehaving. It is a great tool in the hands of administrators and usually brings into attentions things they didn’t know before and allows them to resolve the issues.
However, there are a handful of companies that abuse the abuse mailbox system itself. These companies generate tremendous volumes of outgoing e-mails to thousands of ISPs around the world using automated procedures and are only interested in sending these e-mails and nothing more. One of them, which accounts for most e-mails ever sent, to me at least, is of course no other than IP-Echelon. I will not discuss this company further since I’ve talked about them in the past (Okay, I may discuss them again in the future to document my new policies to deal with them). The problem caused is that in every single day, tens, or hundreds, or even thousands of e-mails may arrive from them, and the actually important e-mails that are typically at most 5, get lost in the noise. Moreover, if the ISP does not have an automated solution for processing them, they waste a lot of man hours trying to reply to or even (better) delete their e-mails.
IP Echelon is a copyright company. If they detect a torrent download, they e-mail the ISP. I get why they do it and what they gain from it and it can be considered acceptable. But there are other companies, that have automated systems in place to report other things, such as comment spam, directory brute forcing (looking for phpMyAdmin, etc.), or other tiny issues. Although these e-mails are much more rare, they are also annoying.
Let me explain to you what these companies do, by using a real example. The example that I will use today is a company called Web Iron. I will be using them for this example as they are the 3rd most annoying company I receive abuse e-mails from.
Web Iron is a typical “security” company with the only exception that their website does not contain the word “cyber” at least 50 times (it doesn’t contain the word even once!). That said, they have a nice image in their home page with what they can(’t) offer: COMPLETE WEB SERVER PROTECTION
That’s right.. 0days? Meh. Nothing can touch your website if you use this solution. Nothing. Because it’s complete protection, remember?
They also include something new, a stock-market-like live attack stream™:

What every SOC needs.
Of course, you shouldn’t forget the obligatory pew pew map, another modern web security necessity:
What? It is just an embedded Google Maps? Oh yeah, that’s because I have Ad Block installed. I guess they didn’t test it with Ad Block because who uses it anyways and it’s not like it improves security or privacy. In case you were wondering though how it looks, here it is, so you don’t have to disable your Ad Block:
The definition of “actionable intelligence”, right?
And here you can see some live statistics that update every now and then:
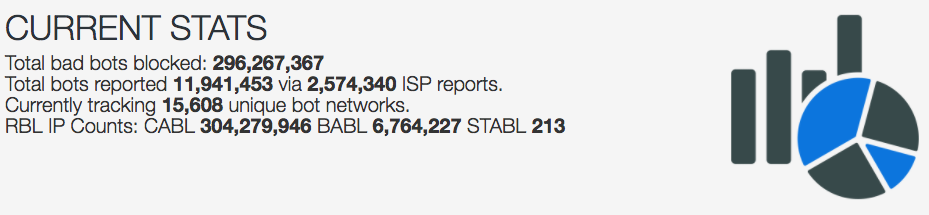
BTW, if their website changes, you can find an archived copy here.
So now that we established the fact that Web Iron is a serious security company that can protect web servers against any and all attackers with the information they have, let’s have a look at one of their e-mails:

Let’s start with an image. Because mail server storage is free and never ends. And let’s have this image in every e-mail.
You are receiving this e-mail in regard to abuse issues against our clients coming from the host at IP 62.141.55.117.
That’s good so far. I can see the offending IP Address right at the top. Now I know which server / client is responsible.
— Automated Message - To get a response or report issues with the reports, please see the contact info below. —
— Report details are at the bottom of the e-mail. For web attacks see the “bot” links for more details about the attack. —-
Okay, it appears the e-mail is automated, and they use some kind of platform to get more information and more information should be below so I can get the necessary information. Got it.
Webiron is a security service and this e-mail is being sent on behalf of our customers. We do not control how our clients configure their protection and as a result do not control how blocks and bans are generated.
Okay.. They are a security company, they know what they’re doing, and if I don’t act, my clients (as an ISP) may be blocked from websites they protect.
We are committed to providing useful information on abuse issues on behalf of our clients to help stop issues related to issues that seem to originate from within your network.
These guys are pros. They will only provide useful information. Wow. I’m really excited about that. I bet the next line is that useful information they’re talking about. Let’s see.
We value your time and effort and appreciate your assistance in handling these issues!
That’s good. At least they value my time, unlike others.. Now let’s see that useful information..
If you are responsible for abuse issues however the IP being reported does not belong to you, please open a ticket or email us to let us know of the error and we’ll correct it as soon as possible.
Wow, they even care about misreported abuse and they want to send these e-mails to the rig… Come on, give me this “useful info”!
Please note due to the retaliatory nature of attackers and the abundance of internet abuse havens and fake hosting companies, we do not give out the exact IP of our clients. If you require further assistance we will be more than happy to work with you. Just open a ticket our contact us with the details below.
I think I understand this one. I should open a ticket with them to start talking if I want more information that the one below. They won’t give me the client’s IP Address because there are bad people on the Internet. Never mind, let’s see the attack info at least..
– Who We Are –
A little about our service, we are a server protection solution designed to help hosting companies, their customers, and SoC departments improve their system security, stability and lower TCO and support costs.
Okay, very nice and concise marketing pitch. These guys are so pros I’ll consider using their services when I address this issue. But why the “o” in “SoC” isn’t capital? Anyways.. I guess it’s for companies with System on Chip departments..
Please feel free to send us your comments or responses.
I think I have a few.. Go on..
If you are inquiring for more information you must disclosed the offending IP.
I have no idea what this means and at this point I’m too afraid to ask.
To contact us via e-mail, use support@webiron.com, however if you require a ticket tracked response you can open one at our SOC ticket system.
Okay, so I guess I’ll either have to reply to them or open a ticket. But let’s read on so I can get the useful information first to know what I’ll tell them..
– Abuse Criteria –
To be considered abusive, a bot must either be a clear danger (IE: exploit attempts, flooding, etc) or match at least two items from the list (Internet Archive)
Hmm, at least what this IP Address did must be serious. I should really spend 48 more hours reading that e-mail and various FAQs to even understand what it did..
– Removal Requests –
To be removed entirely from future reports reply to this e-mail with REMOVE (in all caps) in the subject line. Please note this will only stop the e-mail to the address the e-mail was sent to and public notices will remain as your abuse address will be listed on our BABL blacklist.
Finally. The first piece of useful information. This is what I’ll do right after I finish reading that e-mail.
– Feed/History Links –
IP Abuse Feed: https://www.webiron.com/abuse_feed/62.141.55.117
IP Detailed Information: https://www.webiron.com/iplookup/62.141.55.117
Your Abuse Report History: https://www.webiron.com/abuse_feed/abuse@daknob.net
Aha okay, looks like all their reports are public and available both per IP as well as per abuse e-mail. Very good for transparency.
— Blacklist Warning —
In an ongoing effort to stop chronic abuse we maintain several blacklists available as flat data or free public DNSRBL.
Hmm, looks like their data is made public anyways and I guess that’s good because anyone can use it for free..
For more information see: https://www.webiron.com/rbl.html
For more information? Is this e-mail ending? Where are the details you promised?
To check the blacklist status of the offending IP, see: https://www.webiron.com/iplookup/62.141.55.117
Oh, there’s more. Of course.
– NEW –
We have now opened access to our RBL API allowing direct access to the entire RBL database. For more information please see: https://www.webiron.com/rbl.html
I guess advertisement with abuse e-mails is cheaper than Google Adwords..
Thank you for your support, The WebIron Team
WHAT? Where’s the information you promised me?
Note - All times are in America/Phoenix (-07:00)
Oh nice, there’s more.. I see they stick to standards like UTC.
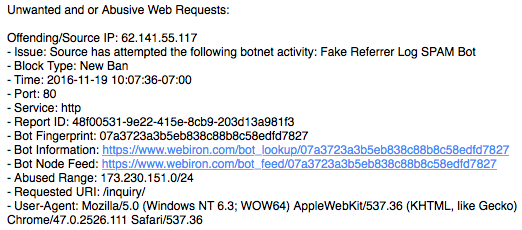
And this is the end of the e-mail. Fake Referrer Log. All this, for someone who set the Referrer to something like “Free SEO TOOLS - www.example.com” and it was written to the web server logs.
Perfect.
And now? What should I do?
The way I currently reply to abuse e-mails (that are serious and not time wasting e-mails like this) is I ask a very simple question to the person that sent me the e-mail:
What do you want me to do?
For me at least, this is the most important information an abuse e-mail should contain. You send me an e-mail to do something. Because something I did wasn’t okay with you. I want to know what’s the problem and what do you recommend me do to fix it.
The above e-mail has both pieces of information required:
I did nothing important / exciting / dangerous. I should unsubscribe from future e-mails.
On a serious note, if you are sending abuse e-mails, automated or not, make sure you provide the two pieces of information above in the very beginning of the e-mail. Nobody cares who you are, what you sell, how to access your API, what you do for a living, how was your last vacation, they only want to do their job. And their job is to read your e-mail, and possibly act based on it. If you can answer two questions, “What did I do wrong?” and “What should I do now?” in the very top of your e-mail, write whatever you want below that, nobody cares. But make sure you include that in the very top, and clearly stated.
Now since in the end of the day, no matter the contents of the e-mail, I have to reply, I tried to do it as professionally as possible:
Dear WebIron Abuse Department, thank you for sending us this report. Although we cannot confirm whether the specific IP Address has performed any attacks, we believe you that this was the case.
As your website correctly identifies this IP Address, it is a Tor Exit Node set up and maintained that has helped users access an uncensored and anonymous web by moving several TBs of traffic. Like every good thing humanity ever made, some people found ways to use it for bad purposes. We are aware of that and we believe the benefits outweigh the disadvantages of running a Tor Exit Node.
Since we are security aware, we understand that this does not help you much and you want to stop it, but keep in mind that those who sacrifice liberty for security deserve neither..
#inspirationalQuote #verySerious
We are also getting attacked by Tor Exit Nodes every now and then but we are refusing to block them in our firewalls because of the collateral damage that this action will cause. Instead, we are using other methods to protect against attacks, but you probably already know that already. The simplest technique is fail2ban configured to block an offender (completely) for 15-30’. If you configure this correctly, it will vastly limit the attacks caused by an attacker. Another more tricky solution that we apply is involving application layer firewalls that block only a specific path (such as /xmlrpc.php) for a specific IP for a specific amount of time, while making everything else accessible.
If you need any advice on how to protect your users without blocking traffic from Tor, we are available to discuss this issue.
Kidding aside, this reply includes something very important that I firmly believe: blocking an IP Address and/or denying access to someone based on things such as an IP Address is not security. It’s security theater.
IP Addresses change multiple times a day, IPv4 addresses may have hundreds or thousands of users behind them, VPNs, Tor, and other similar solutions for anonymity allow you to change IP Addresses every few minutes. Hacked devices, including IoT ones, give attackers access to thousands of IP Addresses. By blocking an IP Address I think you do (much) more harm than good. And you don’t upgrade your security. You only have an illusion of added security.
If you really want to protect against threats such as credential brute forcing in your website, or path searching attacks, or anything similar, blocking an IP Address and then sending abuse e-mails is not the answer. Securing the software and the services behind it is.
Have you ever received an abuse e-mail from Google? facebook? Apple? Microsoft? Amazon?
Personally speaking, I never did. As a matter of fact I don’t think they even have an automated procedure in place to send one. Why? Is that because these companies are never targeted by attackers? Nobody ever tried to brute force a Gmail? Nobody posted spam on facebook? Ever?
Of course not. These companies are some of the largest targets due to the high reward of hacking them. Why aren’t they sending abuse e-mails? How do they protect themselves if they don’t?
These companies do what I think is the right way to protect their services. They invest on securing them. They don’t run around and complain every time someone posts a spam comment. Instead, they try to prevent them from doing it in the first place.
And you may say these companies have billions. And truth be told they do. They have a lot of people working on just securing their websites. Smaller websites like personal blogs, or SME websites don’t have the capital. That’s also true. They can’t afford to hire someone just for that. But I don’t know of any personal website and no SME website that has the complexity of Google either. I also don’t know any such website that is as big of a target as facebook. As a matter of fact, most such websites out there, including this one, use third party software. They don’t write their own. Blogs use Wordpress, Ghost, or even hosted services like Medium and Blogger. e-shops use WooCommerce, Magento, Shopify. They don’t have much to protect: if they use a fairly known platform, follow the security recommendations, don’t do something stupid like admin/admin or phpMyAdmin exposed with default credentials, and update everything, they should probably be fine. You don’t necessarily need billions to make your site secure.
How do you protect your house? Do you leave the door open and every time someone steals something you notify someone even remotely related to the burglar to prevent this from happening again? Or do you lock your door and close your windows?
Exactly.
Then why send abuse e-mails like the one above?
Exactly. No actual reason.
With that, we got the “What did I do?” question out of the way. Nothing bad. It’s just that someone used Tor to write “Free SEO Services - www.example.com” to a WebIron’s client’s Apache logs. Which will be rotated in two days. Wow.
So what should someone do when they received a report like that? In my opinion, nothing. It’s just an automated e-mail, like many others, that just aims at wasting your time. If someone relies on everyone else using the Internet to not attack their site, then sorry, this is never going to happen, and all the time everyone else spends trying to follow that person’s rules is time wasted.
And now, time to unsubscribe from future Web Iron notifications. Once and for all. But how? Well, as we’ve seen before it’s pretty easy:
To be removed entirely from future reports reply to this e-mail with REMOVE (in all caps) in the subject line. Please note this will only stop the e-mail to the address the e-mail was sent to and public notices will remain as your abuse address will be listed on our BABL blacklist.
By hitting the reply button, an e-mail will be sent to bounces_abuse-AT-daknob.net@abuse-reporting.webiron.com and removes_abuse-AT-daknob.net@abuse-reporting.webiron.com. Setting the subject to REMOVE will do it. Right?
Of course not. I tried every possible combination and I still get e-mails with the same content, only with this added:
WARNING: This issue for this IP has been marked unresolved for XX days. As a result your entire organization is in danger of global RBL blacklisting.
So yeah. You can’t unsubscribe. Web Iron will keep e-mailing you, and not only that, even if you reply, nobody will read it, and they’ll keep sending e-mails for every e-mail they sent, every 30 days or 60 days or 90 days or whatever. And they’ll even threaten to “blacklist your entire organization” and maybe also do voodoo to you, I don’t know.
But don’t worry, at least their support is friendly and they’ll help you by ignoring all your tweets to them. Except the one where you threaten to take the matter of what is now spam to their e-mail provider.
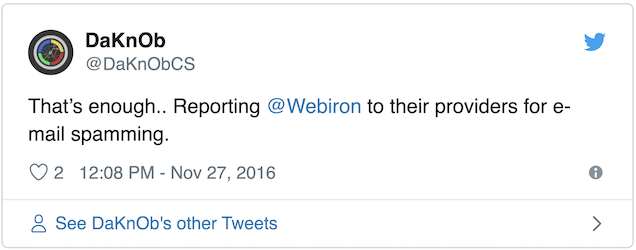
Then, they reply.
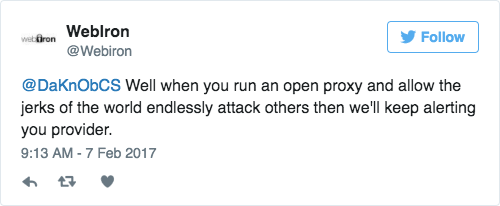
Anyways..
If you take something from this post, I don’t want it to be Web Iron and that they solved the web server security problems once and for all. I want it to be that abuse e-mails can really help.
They can tell a system administrator something they don’t know.
So please, if you think something is worth the time and effort of an administrator, do send them. If one of their DNS servers is misconfigured and participating in DDoS attacks, do send an e-mail. But only send it if you can include the answer to two questions first: “What’s the problem?” and “What should they do?”. Include that in the top of the message, so they can process it quickly. Assume the person reading it is technical. These e-mails don’t go to Sales. Try to avoid sending automated e-mails since these are usually for cases like the above where the recipient can’t do anything.
Also, don’t be Forthnet (and tons of other providers) and read your abuse mailbox. Sure, it has a ton of spam from misbehaving reporters, but there may also be something important there. And often there is.
Some images are © WebIron and are taken from their website, www.webiron.com. They are used according to fair use laws and regulations and no infringement is intended. For more information on legal matters, contact legal@daknob.net.